IT Risk Management Software (ITRM)
Implement our IT risk management (ITRM) software to effectively manage cyber risks, ensure compliance with data privacy regulations, establish IT governance policies, resolve cyber incidents, and stay on top of IT assets.

IT Risk Management
Manage potential risks for IT systems efficiently by using our IT risk management tool to effectively monitor and resolve IT risk and implement effective controls.
Manage IT Incidents
Set up a best-practice IT incident reporting process to capture, escalate, and investigate cyber incidents and monitor cases through to resolution.
How can IT Risk Management Software Solutions reduce cybersecurity risk?
Watch our short video to discover how the Camms IT risk management solutions can support your organisation to mitigate risk and operate in line with data privacy regulations and IT policies.
Watch Video
IT Risk Management Capabilities
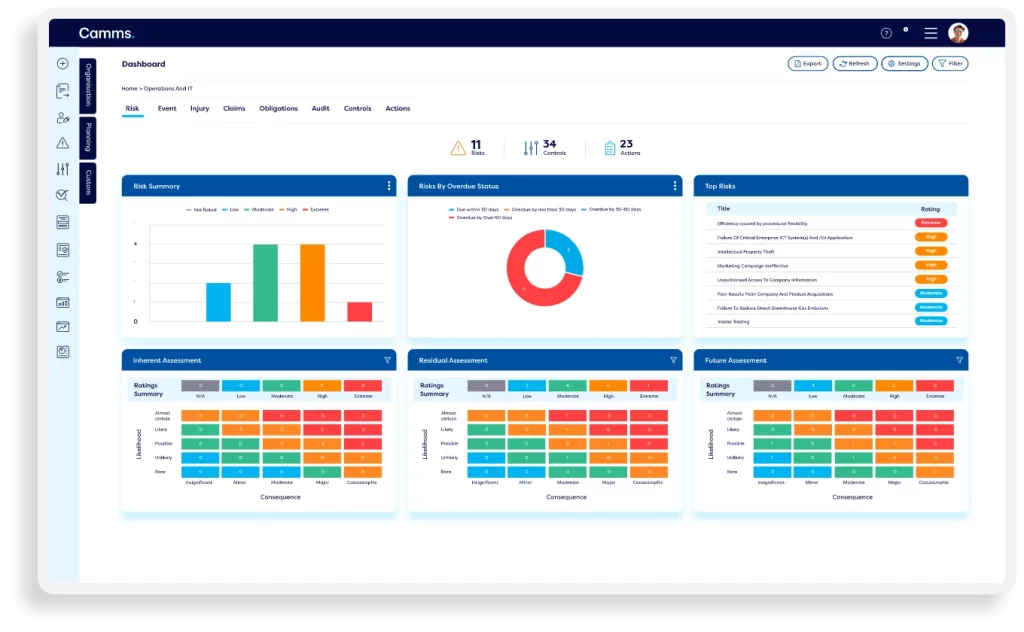
Effectively Manage IT risk and implement sufficient controls
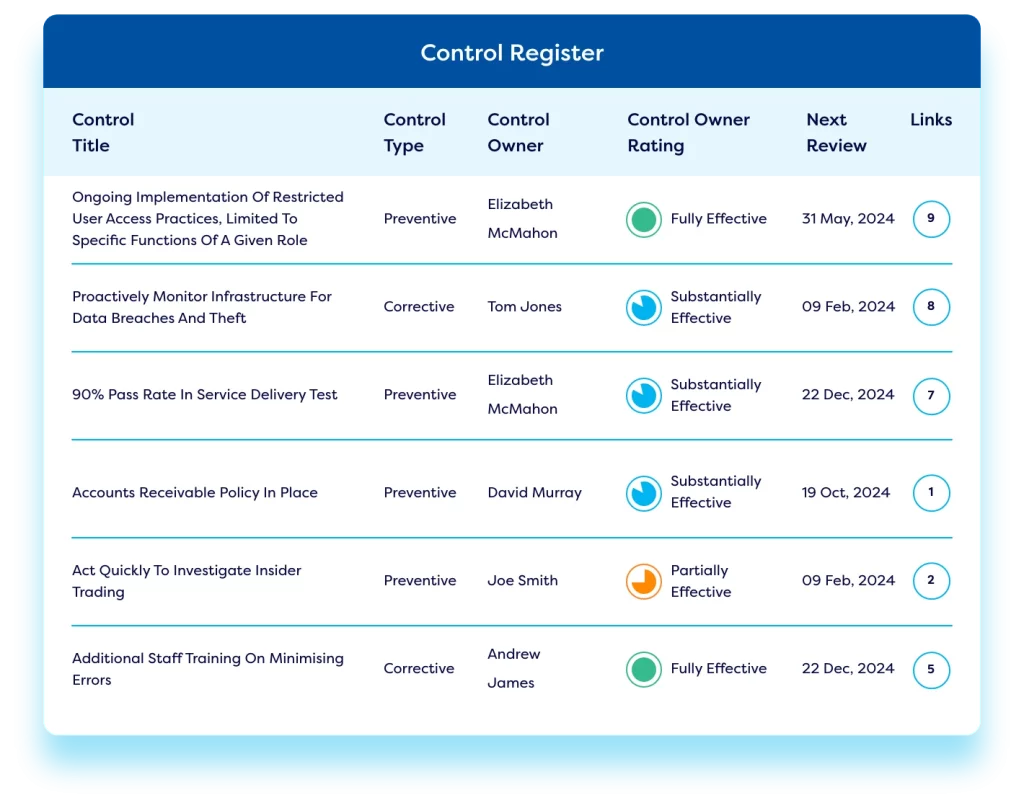
Our IT risk management platform helps companies identify cyber risks, establish IT and cyber risk registers, and conduct online cyber risk assessments. Organisations can conduct assessments online and set Key Risk Indicators (KRIs) and monitor ongoing risk levels.
Automated alerts highlight high-risk areas, enabling teams to ensure fast risk identification, build an effective control library, perform control testing, and link controls back to the originating cyber risks. Automated workflows facilitate risk escalation and the implementation of risk treatment actions.
Report on IT risks & vulnerabilities
Our IT risk solution provides a range of dashboards and reports to analyse potential threats – including heat maps, bow-tie analysis, and interactive Power BI reports.
Personalised dashboards allow each stakeholder to easily view their upcoming actions related to IT risk assessments and control checks. Executives and board members can gain clear insights into IT risk exposure through user-friendly interactive reports and dashboards – empowering them to make informed decisions regarding IT security.
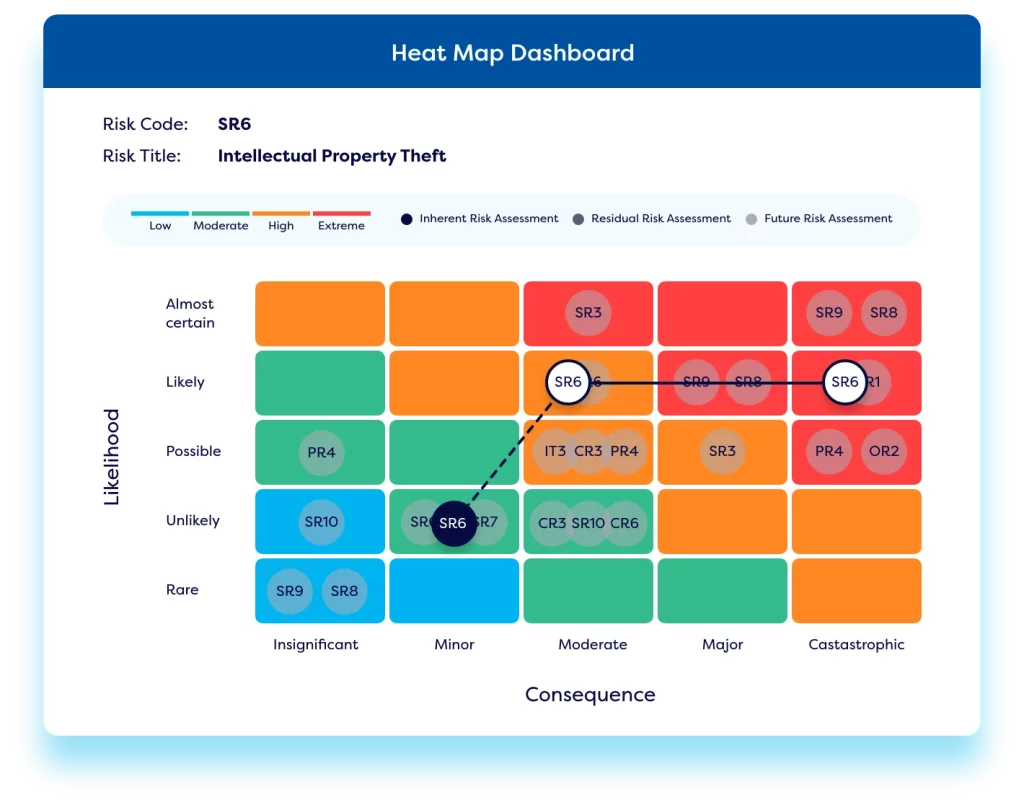
Monitor compliance with information security regulations & policies
Our solution enables organisations to align their processes with complex compliance requirements and industry standards, such as GDPR, ISO 27001, and NIST – using out-of-the-box templates and forms. Compliance obligations can be mapped to relevant policies, controls, and regulatory requirements for traceability – ensuring effective compliance management. Teams can establish a best-practice regulatory change management process to ensure adherence to IT standards and regulations. The solution integrates with leading regulatory content providers like LexisNexis to automatically pull relevant regulatory updates into the platform. Firms can also use our IT compliance software to establish a library of policies within the platform and monitor compliance and track policy updates and approvals.
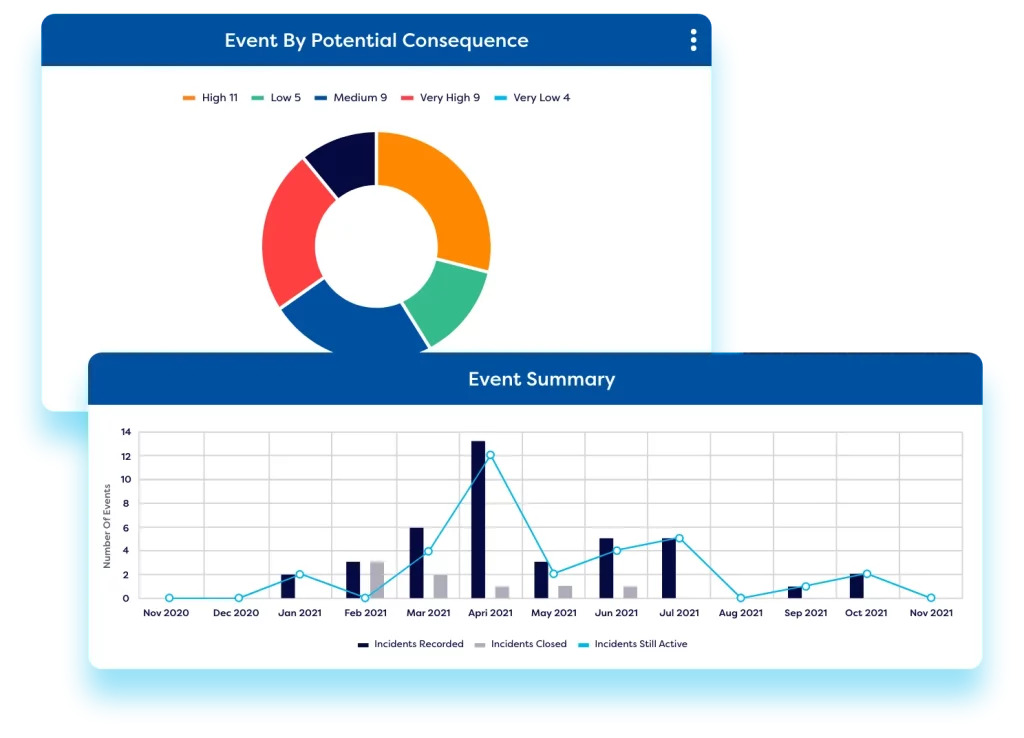
Cyber incident management
Implement a best-practice cyber incident management process within the platform to get proactive oversight of potential IT risks. Incidents can be seamlessly integrated with third-party monitoring and ticketing tools to automatically generate cyber incidents based on events or tickets. Teams can then conduct investigations, root cause analysis, and remediation actions using automated workflows within the ITRM tool. Organisations can link incidents to compliance and risk obligations – facilitating the analysis of potential control failures and highlighting compliance issues and cyber risk exposure.
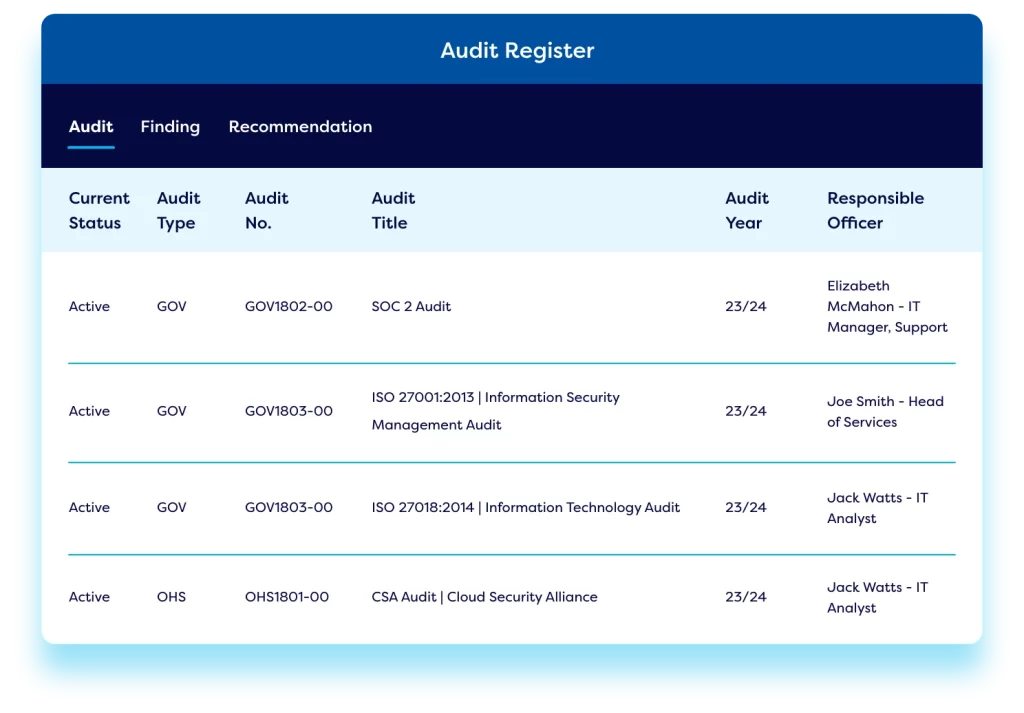
Cyber audit management
Protect the safety of company data by utilising our IT risk tool to plan and schedule both internal and external cyber audits. Track audit recommendations and actions using case management workflows and link audits to relevant risks and risk treatments for deeper insights. Using a cyber security risk management platform to manage cyber audits ensures comprehensive end-to-end traceability and facilitates audit reporting to key stakeholders.
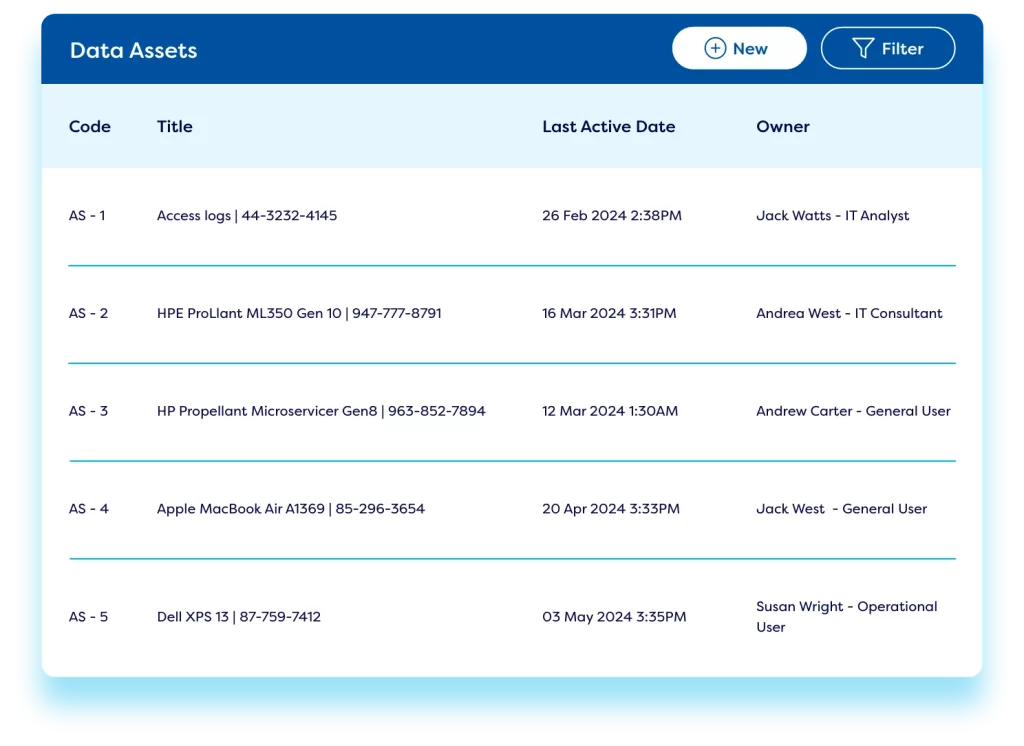
IT asset management
Safeguard your IT infrastructure by keeping all equipment and licenses current and functional using the asset management functionality within our IT risk platform. Our ITRM tool allows you to create online asset management registers to effectively manage hardware usage, software licenses, and physical assets. Built in reports offer an overview of outdated equipment and licenses, streamlining budget planning.
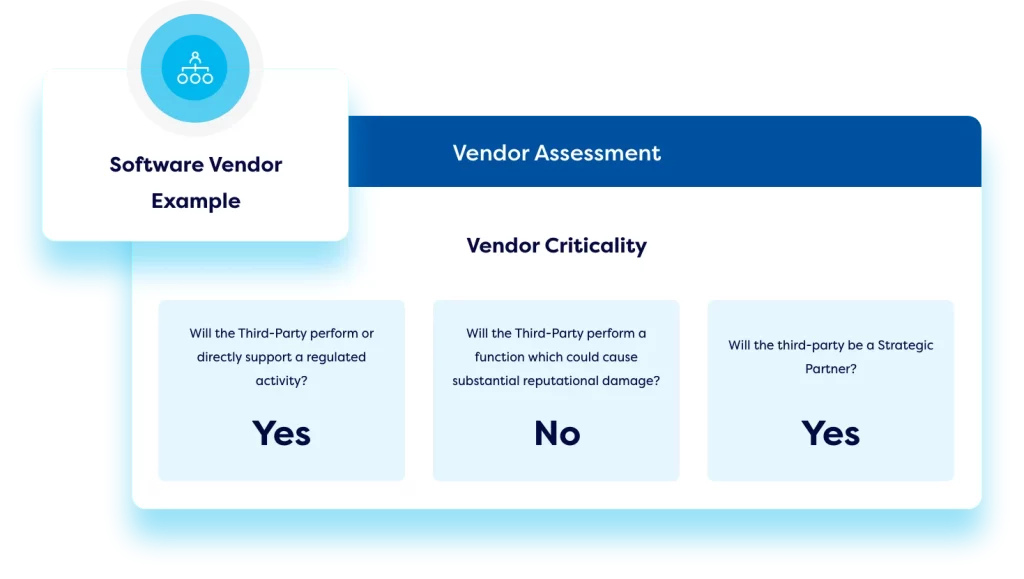
Third-party IT risk management
Create a best-practice third-party risk management process for IT vendors. Build an online vendor library and streamline digital vendor risk assessments with conditional workflows and transparent scoring methodologies to analyze the results. Automate the monitoring of key metrics such as SLAs, KPIs, and industry benchmarks for continuous vendor performance oversight. Easily compare vendors, standardize onboarding and offboarding processes, and manage contract renewals from a central IT risk platform.
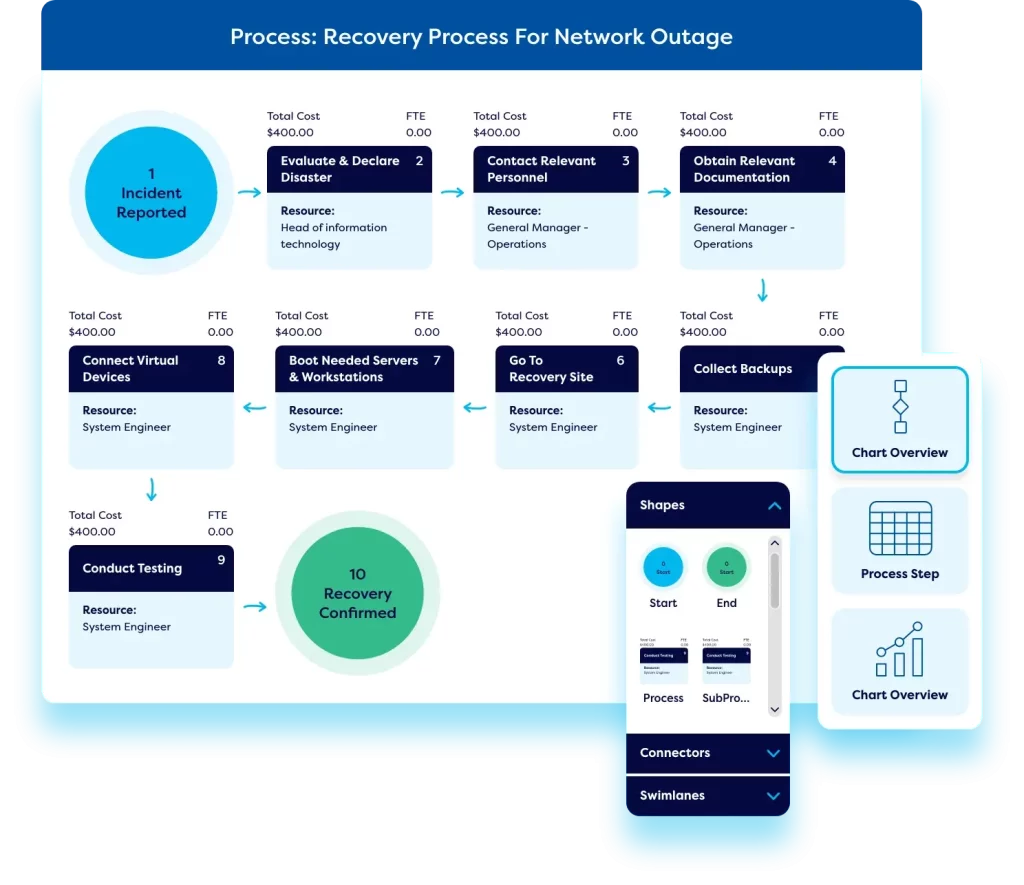
Business continuity & operational resilience
Our enterprise-level IT risk management software includes robust operational resilience capabilities. Teams can formulate a best-practice business continuity planning process, conduct business impact assessments, and perform business process modelling to ensure critical processes remain operational in a crisis. This allows for a clear understanding of an incident’s impact in terms of cost, downtime, and man-hours lost, and automates the implementation of business continuity plans.
Your IT Risk Management Resources
The latest and hottest pieces of IT risk management and cybersecurity content to keep you in the loop.

IT GRC: The Cornerstone of Operational Resilience in the Digital Era
In this eBook we explore 8 key areas that make up a comprehensive IT GRC program – from the intricacies of third-party risk management, IT policies, and audits to the broader GRC considerations of digital risk and compliance.

Cyber Risk Management: Does cyber risk get enough boardroom airtime?
This eBook highlights the threats that businesses are facing today, explains why cyber risk should be at the top of the boardroom agenda, and explains the integral part a GRC tool plays in tackling cyber threats.

10 Ways to Reduce Cyber Security Risk
Every business is at risk of cyber-attacks – with cybercrimes predicted to cost $10.5 trillion per year. Cyber security awareness means empowering the people connected
Why Choose Our IT Risk Management Tool?
Discover more about the Camms IT Risk Management Solution
Frequently Asked Questions Relating to
IT Risk Management Software
IT risk management software platforms are typically online, cloud-based tools that allow organisations to implement effective IT Governance, Risk, and Compliance (GRC) processes.
These tools enable firms to identify and monitor potential cyber and IT risks, perform assessments online, and implement controls to reduce cybersecurity risk. Firms can also use the platforms to proactively manage the risks associated with third-parties, vendors, and suppliers by easily carrying out vendor risk assessments, vendor benchmarking and score carding, and monitoring supplier performance against SLAs and KPIs.
These tools enable firms to create an ‘obligations register’ containing relevant data privacy and information security regulations, legislation, policies, and procedures – enabling firms to understand their IT obligations and monitor adherence. Organisations can also use the platforms to establish a best-practice business continuity planning program, maintain a cyber asset register, and manage and resolve cyber incidents.
The benefits of IT risk management software include:
- Visibility of your cyber risk landscape through insightful dashboards and reports.
- A reduction in time spent on IT risk management reporting and administrative tasks – leaving time to focus on analytics to reduce cyber risk and implement corrective actions.
- A holistic view of IT and cyber risk across your organisation right up to the boardroom.
- Useful insights to guide important business decisions regarding where to allocate budget and resources to reduce cyber risk.
- Reduced risk monitoring and reporting costs.
- ITRM tools help an organisation to overcome challenges in enterprise-wide risk and assurance management by creating a culture that understands cyber risk – building an awareness of cyber risk and the impact of cyber incidents.
- Reduced likelihood of system downtime, data breaches, IT incidents, and data loss by effectively managing cyber risk, ensuring compliance with data privacy regulations, implementing business continuity plans, resolving cyber incidents, and building a risk aware culture.
- Assurance to stakeholders and the board that the organisation is prioritising cyber risk and providing data to support important decision-making.
When selecting an IT risk management software vendor, firms should consider:
- Are there any information security regulations that you must comply with that will affect how you structure your IT risk management program?
- Which framework will you use to rate and categorise IT risk and cyber incidents.
- Can the IT risk management tool be customised to meet any bespoke software company requirements?
- Can the IT risk management platform offer further functionality to grow with you as your organisation and ITGRC processes expand?
- What built-in information security and data protection protocols does the IT risk management tool have?
- Can the IT risk management platform be mapped and integrated with your other systems and data sources via API Integrations to ensure a single source of truth for cyber risk data?
- Which staff need to access the IT risk management application and what information will they input and what statistics do they need to view and report on?
- What key areas do you want to manage in the platform, consider the following; operational risk management, enterprise risk management, cyber risk management, cyber incident management, business continuity planning, data privacy compliance, IT policy management, and asset management.
- Can risk assessments be conducted for IT assets?
- Can the platform enable qualitative and quantitative assessments?
- Does the platform show a unified view of cyber assets, threats, and vulnerabilities for comprehensive risk management of cyber risk?
- Does the IT risk system enable your organisation to track regulatory compliance with cyber regulations such as GDPR, NIST, PCI DSS, HIPAA, SOX, and ISO 27001.
- Does the platform offer cloud-based risk management capabilities ensuring the system is available online and widely accessible?
Key information security processes that can be managed using IT risk management software include:
- Cyber and IT risk management – including building a cyber risk register, performing cyber risk assessments, setting KRIs, and operating within a risk appetite framework.
- Control setting and control checks and testing – including vulnerability testing.
- Cyber and IT incident management.
- IT asset management.
- Business continuity planning.
- Compliance with information security regulatory requirements and data privacy laws by accessing best-practice frameworks to comply with regulations and standards like GDPR, ISO 27001, NIST, HIPAA, and PCI DSS.
- IT policy management.
- Cyber audit management.
- Strategic planning and execution.
- Project management.
Some common key features of IT risk management software include:
- Online forms: This enables teams to carry out risk assessments, control checks, control testing, and incident logging online with all data feeding directly into the platform.
- Automated workflows: This enables firms to formulate step-by-step processes for approvals, escalations, checks, tasks, and action management.
- API integrations: This allows companies to pull operational and IT data from other systems and spreadsheets into and out of the IT risk platform to monitor risk levels against real-life data – ensuring a single source of truth.
- Real-time personalised dashboards: Enabling staff at all levels to view and complete outstanding actions and tasks and view useful data relevant to their roles and responsibilities.
- Instant reporting outputs: Enabling teams to easily visualise cyber risk and information security vulnerabilities so action can be taken.
- Automated notifications: This ensures staff are notified of key information or tasks including:
- Upcoming actions like risk assessments and control checks.
- When risk is ‘high’ and action needs to be taken.
- When control checks or control tests show that controls are ineffective.
- Signoffs, approvals, and escalations.
- Policy approvals, changes, signoffs, and attestations.
- Compliance violations.
- Failed audits.
When selecting and comparing ITRM platforms consider the following:
- Configurable interface: Look for a platform that offers best practice out-of-the-box templates, frameworks, workflows, forms, and reports that can be easily customised to incorporate any bespoke requirements and terminology by your super users without costly implementation fees and coding.
- Information security: Many IT risk platforms offer information security certifications like ISO 27001, SOC type 1 and 2, and cyber essentials to ensure your company data is secure.
- Integrated GRC management: IT risk management and IT GRC is just one area of risk, look for platforms that offer functionality to manage governance, risk, and compliance across all areas of the business including operational risk, enterprise risk, strategic risk, third-party risk, and overall compliance risk and project management.
- Pricing model: Consider the pricing model of the IT risk platform to ensure it meets your budgetary requirements.
- Good user reviews: The best risk management software is highly rated by customers and analysts. For example, the Camms platform was ranked as a strong performer in the recent Forrester WaveTM Governance Risk and Compliance Platforms, Q3 2024 and is highly rated by customers on G2.
- Poor quality cyber risk data – due to a lack of data governance rules – that is housed in disparate spreadsheets and legacy systems.
- Managing risk data from multiple and various forms, spreadsheets, emails, and databases leads to inaccuracies and data entry errors.
- Businesses who don’t use an IT risk management system end up with disparate cyber risk data located in separate spreadsheets – creating siloed data, and an inconsistent cyber risk framework that results in inaccurate cyber risk reporting outputs leading to poor decisions.
- Relying on manual, unautomated processes reduces the speed of cyber risk escalation and risk remediation
- Poor integration between data sources makes it difficult to link cyber and IT risk to the relevant controls in the control library.
- When organisations don’t use a top IT risk management platform, they struggle to compare cyber risk across different sites, departments, and countries due to disparate data and inconsistent cyber risk frameworks.
- If firms are not using a SaaS web-based IT risk management tool, the software won’t receive regular patch updates and releases, meaning the tool could become outdated or lack the latest functionality.
To get started simply request a demo of our IT risk management software
Fill out the form below to see the Camms IT risk management platform in action.

