IT & Cyber Risk Management Software

Compliance Management
Manage compliance with complex standards & data privacy regulations such as ISO 27001, CPS 234, NIST, HIPAA, PCI DSS, SOC 2, and GDPR
Cyber Risk Reporting
Use our cybersecurity tool to identify and monitor IT & cyber risks and vulnerabilities and implement mitigating actions and controls.
Manage Cyber Incidents
Use our cyber risk management software to manage cybersecurity incidents from the initial incident, through to escalation, investigation, and closure.
Cyber Risk Management Tool
Cyber risks and incidents can result in enormous regulatory fines and severely impact operations and erode consumer trust. Consequently, there is increased pressure on GRC professionals to effectively manage cyber risk and IT incidents and implement strict governance to operate in line with data privacy laws and regulations.
To do this well you will need a cloud-based cybersecurity risk management platform to get full visibility of risks and cyber incidents and manage them effectively. Read about how cyber threats impact the energy and utilities sectors.
How can Cybersecurity Risk Management Software mitigate risks and keep executives informed?
Watch our short overview video to find out how Camms offers a fully integrated cyber risk management solution to support organisations with their IT and cyber risk management.
IT & Cyber Risk Management Platform Capabilities
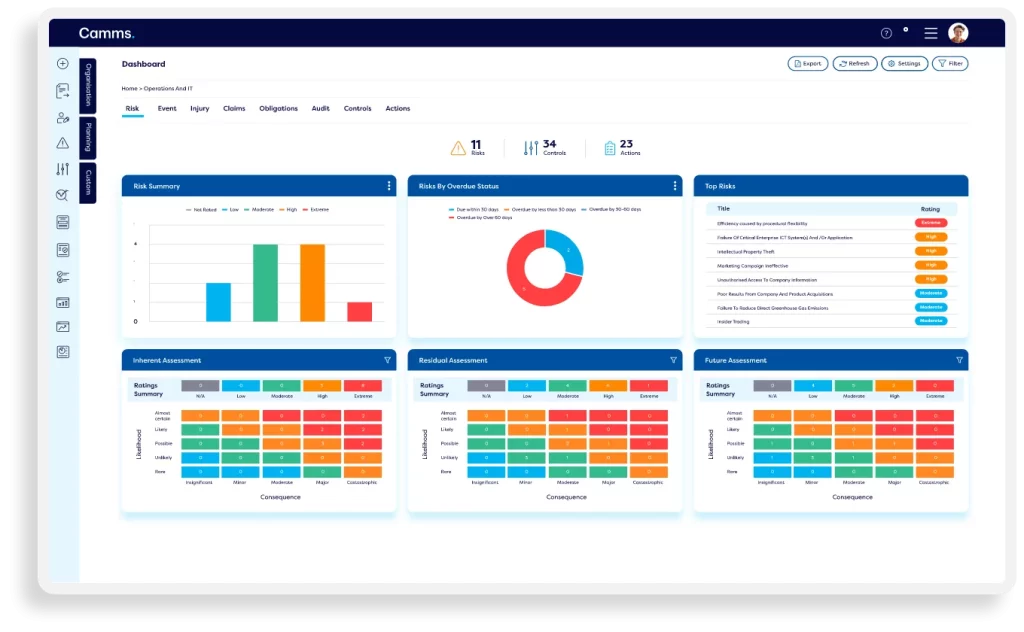
Manage IT & Cyber Risks and Implement Controls
Our cyber risk management solution enables firms to identify cyber risk, establish IT & cyber risk registers, roll out online cyber risk assessments, and conduct security risk assessments. Organisations can use our cybersecurity risk management solution to establish Key Risk Indicators (KRIs) and monitor ongoing risk levels to detect vulnerability. Automated alerts highlight high risk areas. Teams can build an effective control library, carry out control testing, and implement vulnerability management. Firms can use the system integrations and mapping capabilities to link controls back to the originating risks. Automated workflows enable teams to escalate risk and implement risk treatment actions – ensuring effective cyber security risk management. Our IT & cyber risk management platform enables firms to implement a best-practice IT risk management program, introduce robust cyber security measures, reduce cyber security threats, and ensure an enterprise-level approach to cybersecurity risk.
Report on IT & Cyber Risks and Control Effectiveness
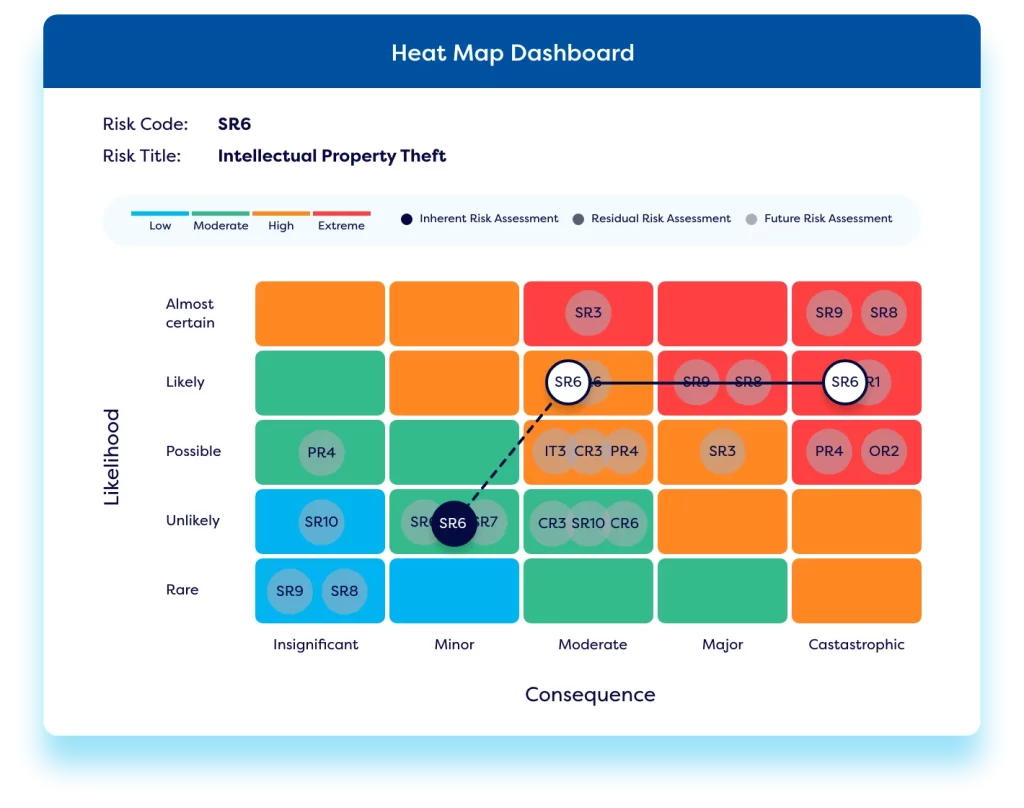
Our cyber risk management software offers a variety of dashboards & reports to understand cyber risk exposure and cyber risk quantification – including heat maps, bow-tie analysis, and interactive Power BI reports. Personalised dashboards ensure each stakeholder can easily view their upcoming actions relating to cybersecurity risk assessments & control checks. Executives and board members can understand cyber risk through clean and easy to understand interactive heat maps and dashboards.
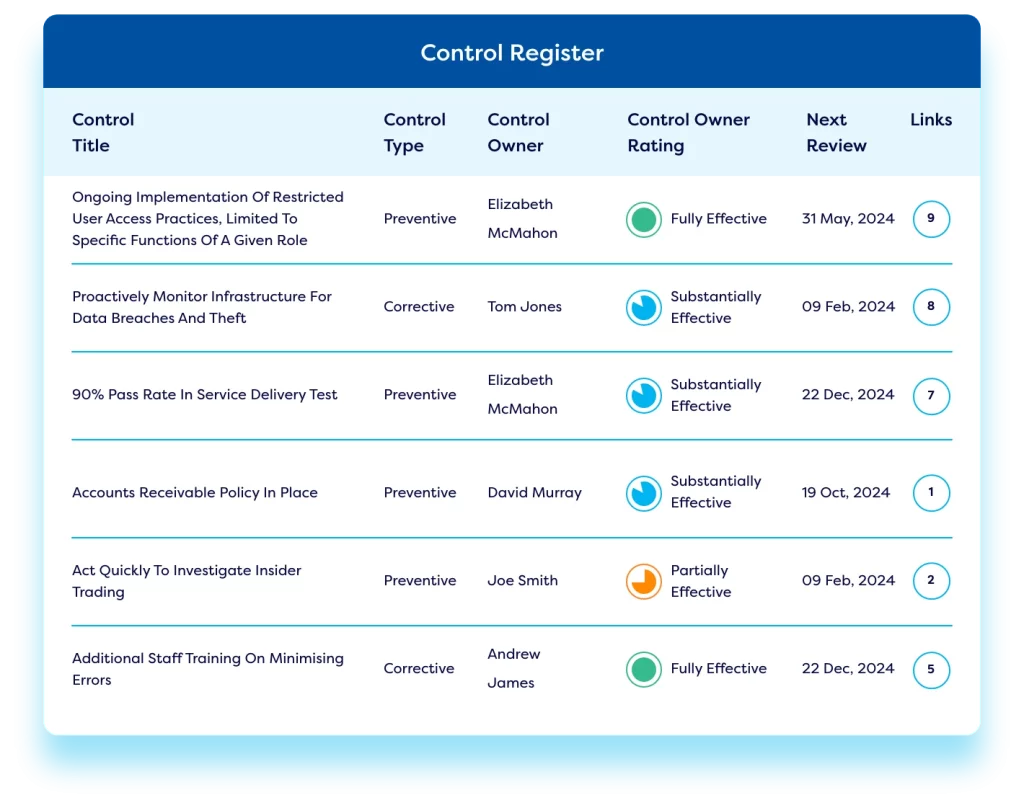
Ensure Compliance with Key Information Security Frameworks
Our cyber risk management tool allows organisations to structure their processes in line with complex compliance requirements including GDPR, ISO 27001, and NIST – using out-of-the-box templates and forms. Compliance obligations can be mapped to relevant policies and controls for traceability. Teams can implement a best-practice regulatory change management process to ensure compliance with IT standards and regulations. The solution integrates with leading regulatory content providers like LexisNexis to pull regulatory updates straight into the platform.
Cyber Incident Management
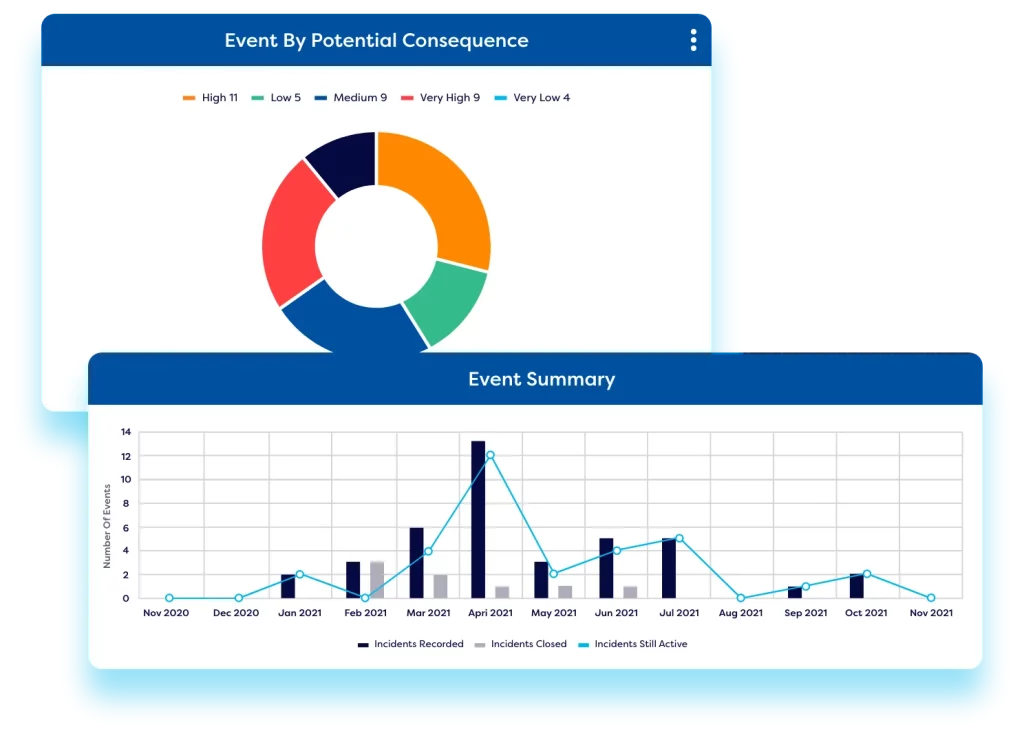
Incidents can be integrated with third-party monitoring and ticketing tools, to automatically create cyber incidents based on events or tickets. Teams can then complete the investigation, root cause analysis, and remediating actions within the Camms cyber risk management tool. Organisations can link incidents to risks & compliance obligations enabling analysis of potential controls that are failing – flagging compliance failures and risk exposure and mitigating IT and cyber risks.
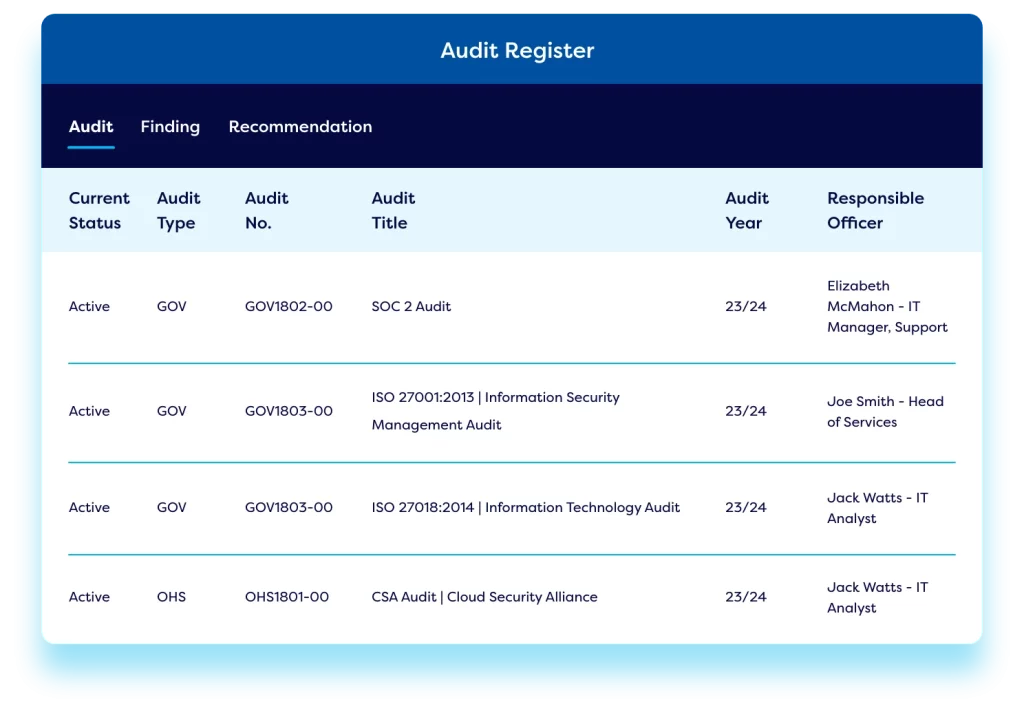
Cyber Audit Management
Use our cybersecurity tool to plan and schedule internal & external audits. Track recommendations and actions by linking audits back to risks and risk treatments where relevant. This provides complete end-to-end traceability and enables reporting to key stakeholders.
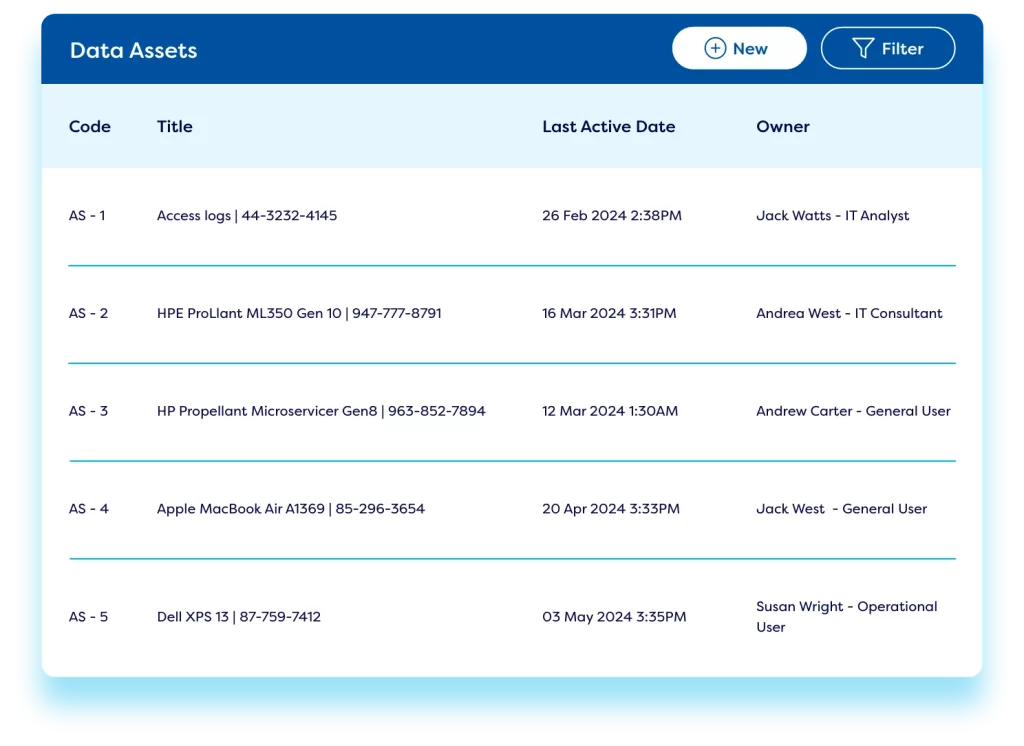
Cyber Asset Management
Safeguard your IT infrastructure by ensuring all equipment and licences are up-to-date and fit for the job with our asset management capabilities. Use our cybersecurity risk management tool to create online asset management registers to effectively manage usage of hardware, software licenses, and physical assets. Reports provide an overview of out-of-date equipment & licences – simplifying budget planning.
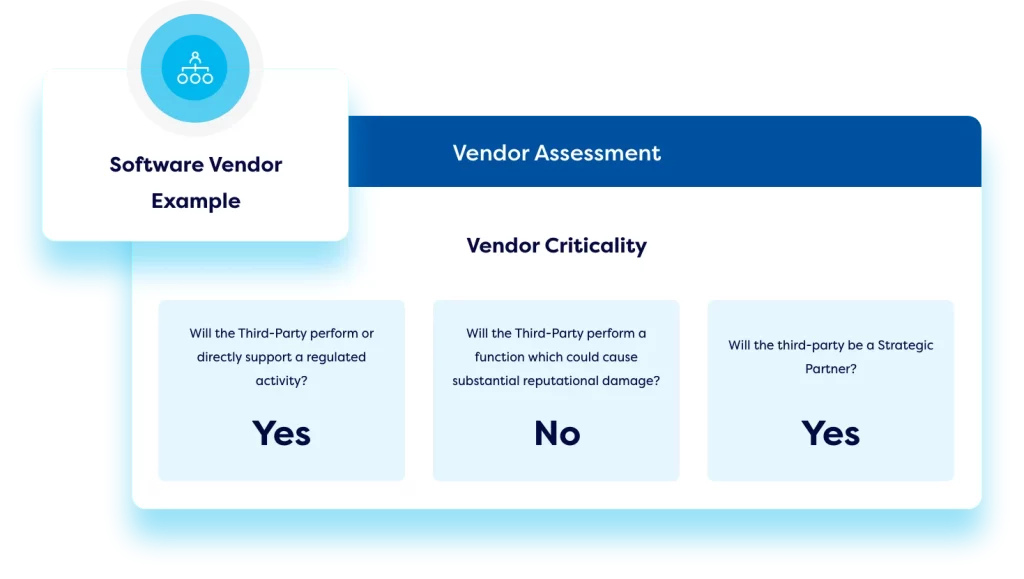
Third Party Cyber Risk Management
Create an online vendor library. Roll out vendor risk assessments with conditional workflows and transparent scoring methodologies. Implement automated monitoring of key metrics like SLAs, KPIs, and industry benchmark standards to provide continuous oversight of vendor performance. Easily compare vendors, standardise the onboarding and offboarding process, and manage contract renewals centrally.
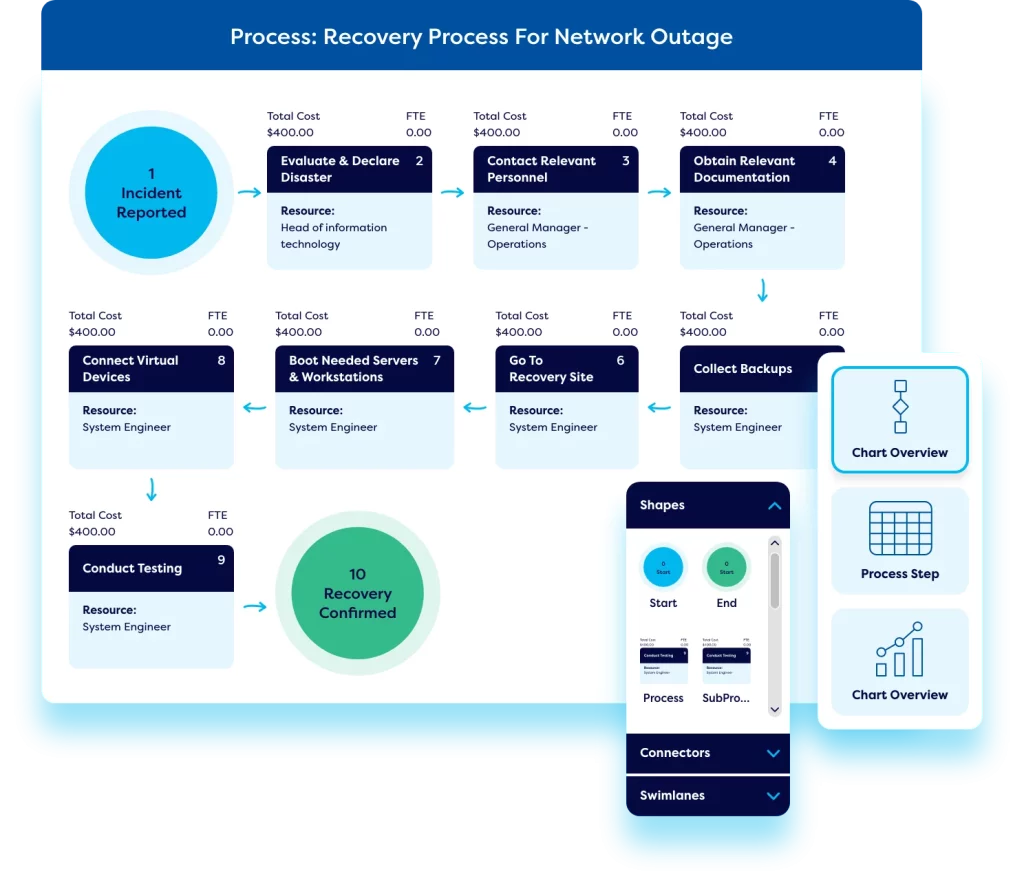
Operational Resilience
Our cyber risk management software also offers operational resilience capabilities. Teams can create a library of BCM plans, and carry out business impact assessments, and business process modelling – making it easy to understand the impact of an incident in terms of cost, downtime, and man hours lost and automate the implementation of business continuity plans.
Your IT & Cyber Risk Management Resources
The latest and hottest pieces of cybersecurity risk management content to keep you in the loop.

IT GRC: The Cornerstone of Operational Resilience in the Digital Era
In this eBook we explore 8 key areas that make up a comprehensive IT GRC program – from the intricacies of third-party risk management, IT policies, and audits to the broader GRC considerations of digital risk and compliance.

Cyber Risk Management: Does cyber risk get enough boardroom airtime?
This eBook highlights the threats that businesses are facing today, explains why cyber risk should be at the top of the boardroom agenda, and explains the integral part a GRC tool plays in tackling cyber threats.

10 Ways to Reduce Cyber Security Risk
Every business is at risk of cyber-attacks – with cybercrimes predicted to cost $10.5 trillion per year. Cyber security awareness means empowering the people connected
Get started and request a demo
Fill out our simple form to see Camms’ cyber risk management solutions in action.

