Vendor Risk Management Software
Use our vendor risk management software to gain a thorough understanding of the risks posed by your vendors, suppliers, and service providers. Build a vendor database, automate vendor risk assessments, apply robust controls, and monitor performance against SLAs, KPIs, and compliance requirements. Enable effective management of third-party risks and secure your supply chain.

Track Vendor Performance
Develop a centralized vendor repository to store critical information on contracts, costs, SLAs, and KPIs, allowing continuous monitoring of supplier performance against key metrics.
Streamline Vendor Risk Assessments
Utilize our vendor risk management software to automate vendor risk assessments. Both employees and suppliers can complete assessments through online forms, with all data seamlessly flowing into each vendor’s profile within the platform.
External Vendor Portal
Provide third parties with access to a vendor portal where they can complete questionnaires, surveys, and risk assessments online—collecting comprehensive data to enable thorough vendor comparison and risk evaluation.
Third-Party Risk Insights
Our vendor risk management software links with risk intelligence providers through APIs to provide detailed insights on potential red flags relating to your suppliers, covering areas such as ethical practices, financial health, legal and regulatory compliance issues, and cybersecurity threats.
Vendor Risk Management Software Capabilities
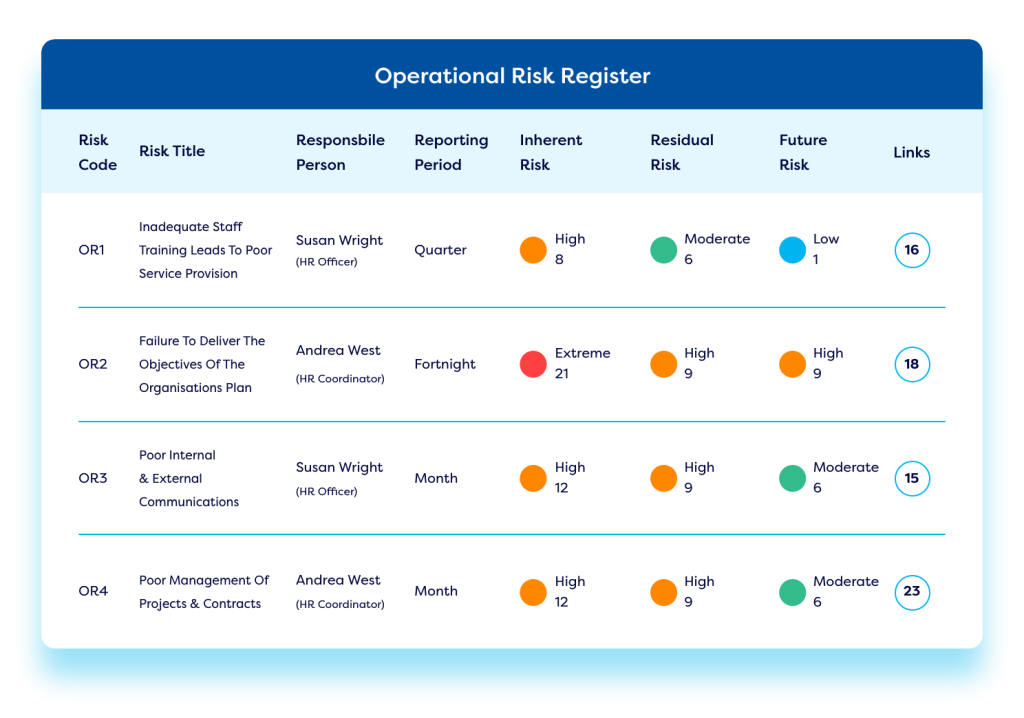
Establish a Vendor Register
Establish an online vendor log within our vendor risk management software to capture essential supplier details, including costs, contracts, key contacts, Service Level Agreements (SLAs), and Key Performance Indicators (KPIs) – creating a centralized third-party inventory. Structure a best-practice onboarding and offboarding process, conduct vendor risk assessments, and apply score-carding and benchmarking for each supplier. All information is seamlessly synced to each vendors’ profile, enabling easy comparisons and clear performance ratings – enabling prompt action on any underperforming service providers.
Automated Vendor Risk Assessments
Your stakeholders can complete vendor risk assessments online, with data automatically feeding into the vendor risk management platform for immediate oversight. Organizations can customize forms for different supplier categories, ensuring all critical evaluation criteria are captured within routine supplier risk assessments. Camms’ supplier and vendor risk assessment software uses workflows to automate the distribution of vendor risk assessments and to chase outstanding actions. Firms can design detailed questionnaires, assess key supplier attributes, and use workflow paths to guide teams through responses to streamline approvals and signoffs. Automation also supports regular vendor reviews with alerts and workflows that track the progress of corrective actions as needed.
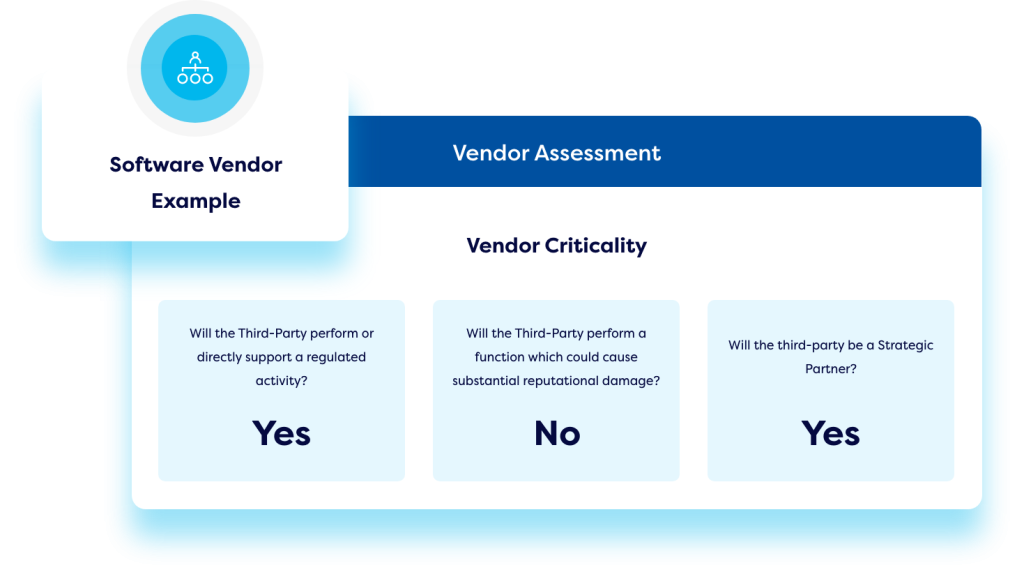
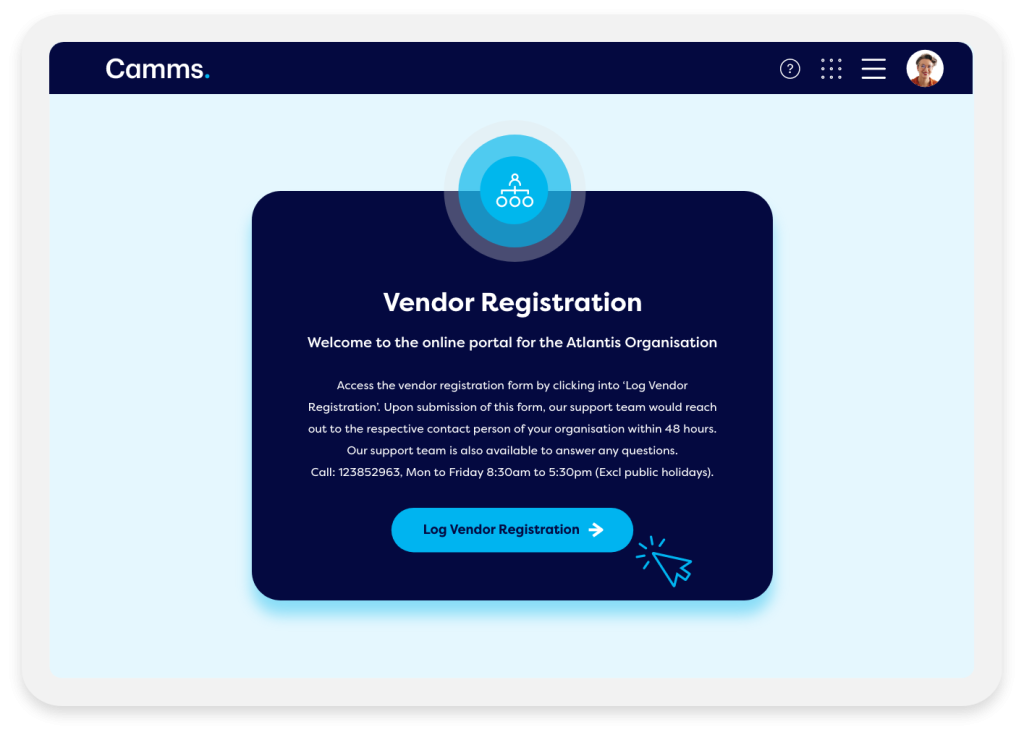
Online Vendor Portal
Camms’ third-party risk management portal simplifies vendor assessments by removing the need for manual emails and consolidating vendor responses in one place. Vendors can log in via an online portal to complete questionnaires and surveys online, with results captured instantly and integrated into the system’s broader workflow. Upon submission, completed assessments can automatically trigger alerts and initiate subsequent steps for internal teams, streamlining and enhancing third-party risk management.
Controls and Risk Mitigation
Establish an online control library to implement measures that mitigate vendor risks effectively. Conduct regular control checks and testing to ensure controls remain functional and effective. When risk levels exceed tolerance, use automated workflows to capture and document the actions taken to reduce or address the risks. Setting robust controls helps protect the organization from reputational damage caused by poorly performing vendors.
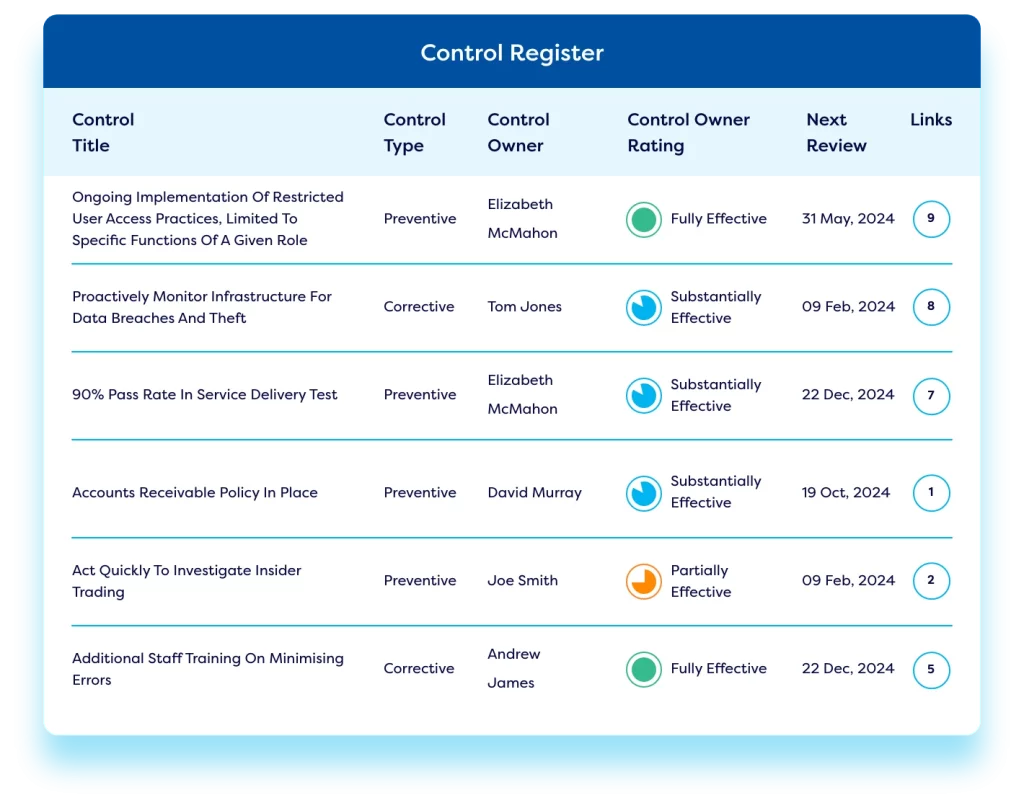
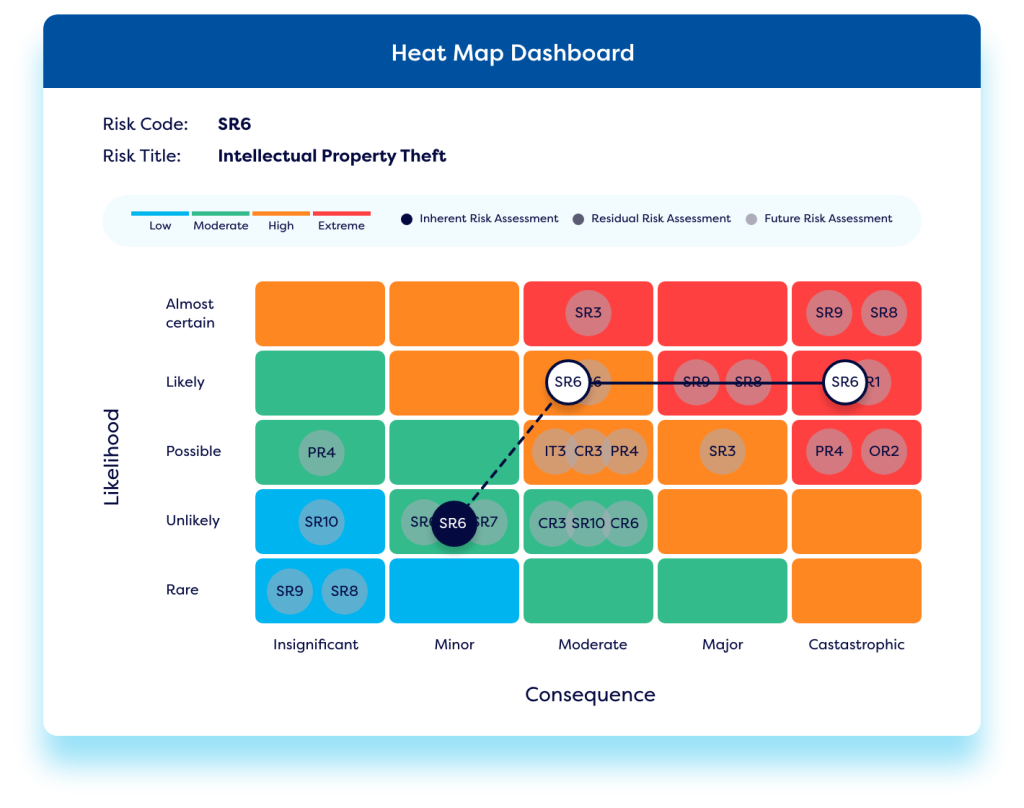
Real-time Dashboards & Reporting
Our vendor risk management solution enables organizations to generate comprehensive vendor risk reports on vendor risk exposure, providing executives with a clear view of supplier dependencies and the associated risks. It includes performance tracking against KPIs, SLAs, and industry benchmarks, ensuring continuous oversight of third-party risks and performance. This holistic view of supplier risk supports informed decision-making and enhances operational efficiency.
Third-Party Risk Insights via API Integrations
Boost your supplier risk management program by using API integrations to connect vendor profiles with external risk intelligence sources for proactive risk identification. This allows you to receive real-time data on supplier financial stability, sustainability scores, sanction lists, cybersecurity ratings, and more. These updates are automatically synced to the vendor’s profile within our vendor risk management software, enhancing vendor oversight and empowering you to manage supplier risk with confidence. This vendor intelligence enables firms to easily address cybersecurity and data privacy threats stemming from third-party vendors.
Regulatory Compliance Management
Ensure your vendors and suppliers adhere to all applicable compliance standards with the compliance tracking features in our vendor compliance software. Regulatory compliance functionality is fully integrated into the third-party risk management framework, providing easy access to essential compliance requirements and incorporating them into vendor assessments – promoting seamless and transparent compliance during supplier audits.
Your Vendor Risk Management Software Resources
The latest and hottest pieces of vendor risk management content to stay in the know.

Using Automation to Build a Consolidated View of Third-Party Risk
In this eBook, experts explain what an effective third-party risk management programme looks like. They share tools & techniques to automate the vendor risk management process and reveal how organisations can get a holistic view of vendor risk.

3 Ways to Automate Third-Party Risk Management
As organizations increasingly rely on external networks, the imperative to monitor and evaluate these third-party relationships intensifies. Third-party risk management automation grants insight into vendor

From Excel to Excellence: Turning Your Risk Data into Insights & Decisions
In this eBook, we explore why spreadsheets are outdated for risk management and help you to identify if your business is ready to swap spreadsheets for an automated GRC solution. Plus, we detail the top 10 reasons to switch from spreadsheets to software.
Why Choose Camms for Vendor Risk Management Software?
Aligning Vendor Risk with Business Goals
The Camms vendor risk management solution aligns vendor risk with your organization’s goals and processes, enabling your team to choose low-risk, high-performing suppliers that are in alignment with your risk appetite and long-term strategic objectives.
Comprehensive Data Security & Privacy
The Camms vendor risk platform is designed with robust security features and certified to industry standards such as SOC Type 1&2, ISO 27001, and Cyber Essentials. It incorporates advanced permissions, encryption, and audit trails to ensure data privacy and comply with IT security regulations.
Discover more about the Camms’ Vendor Risk Management Software
Frequently asked questions about
vendor risk management software
Vendor risk management involves identifying, assessing, and addressing the risks associated with outsourcing business functions to third-party vendors & suppliers. Firms often rely on external partners for critical services such as IT support, supply of materials, financial services, and contract work, which can introduce potential vulnerabilities if not properly managed. Effective vendor risk management ensures that these external partners do not pose security, compliance, or operational risks that could harm the organization’s reputation or disrupt its services.
To mitigate these operational risks stemming from suppliers and prevent supply chain interruptions, businesses typically perform thorough due diligence on potential vendors, including background checks, financial stability assessments, and compliance evaluations. Ongoing monitoring and periodic audits are also crucial to detect and manage emerging risks throughout the duration of the vendor relationship. This includes conducting regular vendor risk assessments, completing compliance audits, and tracking vendor performance against Service Level Agreements (SLAs) and Key Performance Indicators (KPIs). Vendor risk management also involves ensuring suppliers and third parties are complying with various regulations and frameworks.
Vendor risk management software is a platform designed to help organizations effectively identify, assess, and mitigate risks associated with their external suppliers and partners. These solutions typically include features such as automated online vendor risk assessments, real-time performance monitoring, integration with third-party risk intelligence providers, and compliance tracking. By streamlining the entire vendor evaluation process across all third party relationships—from initial vetting to ongoing oversight—these platforms enable proactive management of vendor risks. These vendor risk platforms enhance and simplify the management of vendor and supply chain risks, including cybersecurity threats linked to IT vendors.
These solutions often offer industry best practices and frameworks for vendor risk assessments, such as standardized evaluation methods, supplier due diligence processes, and contingency planning. Adopting a vendor risk management tool helps organizations better identify supplier vulnerabilities, maintain compliance, and protect their business interests while working with external vendors.
Key vendor risk management software features include:
Vendor Library: Build an online, centralized repository that stores key information on all your vendors, including contracts, pricing, key contacts, SLAs, and KPIs. This library allows for easy vendor comparisons and the creation of detailed profiles for each supplier for effective monitoring of third party risk.
Online Automated Risk Assessments: This functionality enables both staff and vendors to complete risk assessments via online forms that automatically update each vendor profile in the platform. Customize these forms for different types of vendors and automate the distribution and reminders for regular risk assessments using workflows.
Real-Time Risk Monitoring: Leverage the supplier risk management software to monitor vendor risks in real time using risk assessment results and threat intelligence data. Link your vendor risk register with supplier performance data through APIs to track risk levels to strengthen your TPRM program.
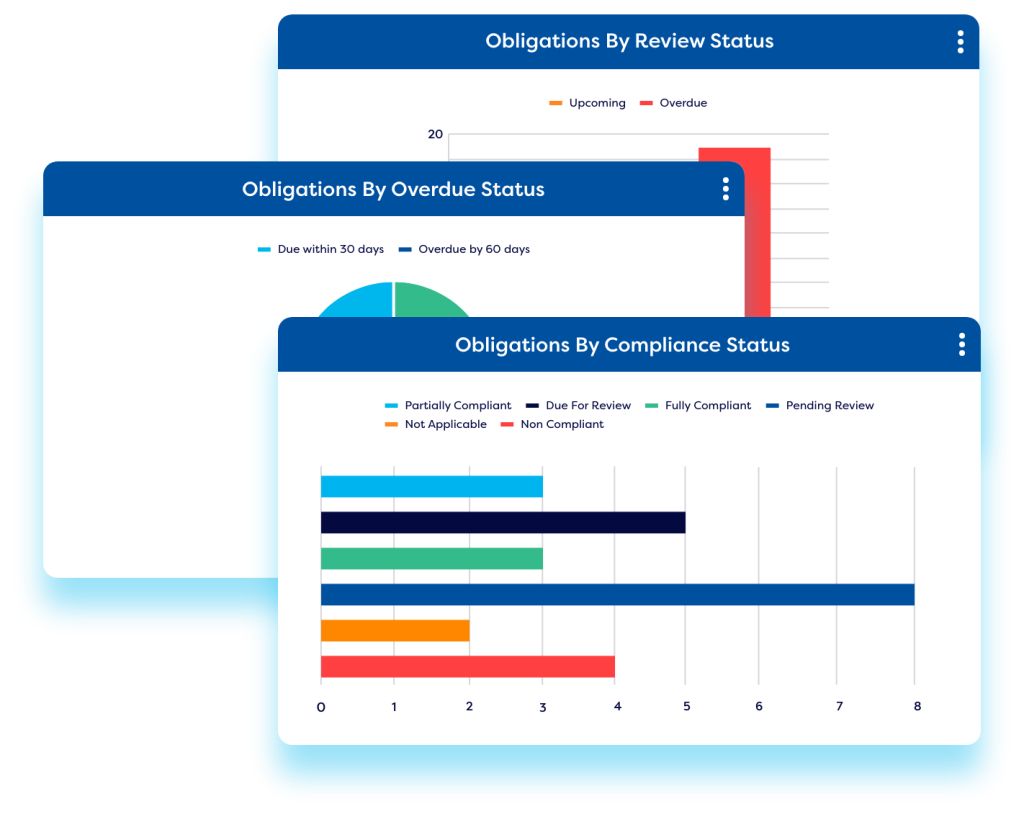
Robust Reporting Features: Access detailed dashboards and reports to monitor vendor risk levels and performance. These real-time reporting tools help organizations proactively identify, assess, and address risks associated with third-party relationships.
Third-Party Risk Intelligence: Integrate the VRM platform with external risk intelligence providers to assess potential threats from third parties, including financial stability, legal issues, data breaches, compliance violations, and other operational risks.
Automated Workflows: Use workflow automation to implement best practices, ensuring any emerging vendor issues are quickly escalated and resolved efficiently.
Vendor Compliance: Many supplier risk management platforms feature tools to track vendor compliance with regulatory standards, helping organizations partner with reliable and certified suppliers.
Attack Surface Monitoring: This involves the continuous process of identifying, assessing, and managing the external-facing vulnerabilities in an organization’s network and systems that could potentially be exploited through third-party vendors, suppliers, or partners. Vendor risk management software supports this by identifying external touchpoints, continuous vulnerability scanning, monitoring vendor security posture, real-time alerts, and the prioritization of risk assessment results – with a view to minimizing the attack surface.
The importance and benefits of utilizing vendor risk management software to effectively manage the risks associated with external service providers, product suppliers, and vendors include:
- Increased Efficiency: Streamlining risk assessment processes reduces the time and effort required to evaluate and monitor third-party risks, improving the overall effectiveness of your vendor risk management program.
- Enhanced Risk Intelligence: Integrations with third-party risk intelligence providers deliver valuable insights into supplier-related issues, such as IT security threats, credit history, and compliance concerns.
- Improved Visibility: Vendor risk management solutions offer enhanced visibility by providing real-time dashboards & reports based on current supplier performance and risk assessment data.
- Reduced Administrative Burden: Automated workflows, online forms, and reporting outputs significantly cut down on administrative tasks, boosting efficiency in managing third-party risks.
- Effective Risk Reduction: TPRM solutions feature active control libraries, third-party risk intelligence, regular assessments, and automated workflows to implement risk mitigation strategies, reducing vendor-related risks.
- Accelerated Risk Response: Vendor risk automation tools swiftly gather and analyze vendor data, flagging potential risk and compliance issues in real time, allowing organizations to quickly respond to emerging threats and disruptions.
- Enhanced Accuracy and Consistency: The best vendor risk management software offers data governance automation to ensure consistent and accurate vendor risk data by applying standardized criteria, reducing human error and maintaining uniformity across evaluations.
- Informed Decision-Making: Third-party risk management platforms provide essential risk intelligence that supports informed decisions when selecting and managing vendors.
- Comprehensive Vendor Risk Management: TPRM solutions address various types of third-party risks—reputational, cybersecurity, strategic, and compliance—enabling thorough assessment, management, and continuous monitoring of vendor risk.
- Seamless Integration: Vendor risk management solutions facilitate the integration of third-party services into core business functions, ensuring vendors meet industry standards, compliance requirements, SLAs, and KPIs.
- Technology-Driven Value: Technology-enhanced vendor risk management programs improve the value of your vendor network and supply chain, ensuring compliance, profitability, and resilience.
- Automated Assessments: Vendor risk management platforms automate third-party risk assessments, delivering timely and easily reportable results.
- Enhanced Accountability: Third-party risk management solutions automate the implementation of risk mitigation plans via workflows and this ongoing monitoring of third-party performance improves accountability and reduces risk levels.
- Minimized Disruption: Effective vendor risk assessment software helps minimize the impact of supply chain disruptions and ensures regulatory compliance across the vendor network.
- Reduced IT Security Risk: These specialized vendor risk tools assess, monitor, and mitigate security risks to strengthen supply chain resilience and protect company data from cybersecurity threats and vulnerabilities.
When selecting a vendor risk management software platform, firms should consider the following:
- Integration with Risk Intelligence Providers: Ensure that the vendor risk platform connects with external risk intelligence sources to provide real-time updates on supplier-related risks such as financial difficulties, IT security breaches, data privacy concerns, and regulatory fines.
- Risk Categorization and Rating Framework: Look for third-party risk management tools that enable the organisation to establish a clear framework for categorizing and rating vendor risks to maintain consistency across the enterprise.
- Customization for Internal Requirements: Check that the vendor risk management platform can be customized to suit your organization’s specific needs, including the ability to modify vendor risk assessment forms and automated workflows to effectively manage different types of vendors and the risks they pose.
- Configurability: Evaluate whether the vendor risk management software can be tailored to fit your organization’s unique processes and requirements.
- Scalability: Assess if the platform can grow with your organization, adapting to your evolving vendor risk management and compliance needs. This may include future capabilities for enterprise risk management, regulatory compliance, ESG, incident reporting, health and safety, business continuity, and project management.
- Data Privacy and Security: Review the data privacy and security features of the third-party risk management solution, including any additional security measures, to ensure they align with your IT team’s requirements.
- Integration with Existing Systems: Verify that the vendor risk platform can integrate with your existing systems via APIs, ensuring a unified source of truth for third-party risk data and enabling real-time monitoring.
- User Access and Data Needs: Consider the platform’s users, the types of data they will input, and the reports and metrics they need, including the format and frequency of those reports, to ensure the vendor risk management platform meets all stakeholder requirements.
- Flexible Pricing Model: Evaluate the pricing structure of the vendor risk management platform to ensure it provides flexibility based on user count and the number of modules, allowing you to pay only for the features you need.
- Comprehensive Reporting: Look for vendor risk management software vendors that offer robust reporting features to empower leadership teams with the insights needed to make informed vendor selection decisions.
- Alignment with ISO 31000: Ensure that the supplier risk management solution is aligned with your organization’s internal risk and compliance frameworks and adheres to the best practices outlined in ISO 31000.
The key features of vendor risk management software include:
Customizable Risk Assessment Forms: Choose vendor risk assessment tools that allow for the customization of online risk assessment forms. The best vendor risk solutions let you tailor assessments for different vendor types, with all data automatically integrated into the platform for accurate evaluations based on specific needs and industry standards.
Detailed Vendor Profiles: Select a vendor risk management tool with an online vendor library that allows you to create comprehensive profiles for each key vendor. These profiles should capture contract details, costs, key contacts, SLAs, KPIs, and relevant risk intelligence, along with assessment results and risk scores to facilitate best-practice vendor management.
Online Vendor Portal: Look for vendor risk management software that includes an online vendor portal, enabling third-party vendors to complete questionnaires, surveys, and risk assessments online. Data from these submissions should seamlessly integrate into the supplier risk management system for streamlined tracking.
API Integrations: Opt for vendor risk management vendors that offer software that supports API integrations to import transactional data related to supplier performance. This feature helps you efficiently monitor risk levels and track compliance with SLAs and KPIs across your entire vendor network and supply chain.
Continuous Risk Monitoring: Choose vendor risk management tools that integrate with risk intelligence providers, ensuring continuous monitoring of suppliers for financial stability, compliance issues, cybersecurity threats, fraud, and other critical risks that could impact your business.
Robust Reporting and Analytics: Look for vendor risk management solutions with strong reporting and analytics capabilities. These platforms should provide detailed dashboards and reports on third-party risk exposure and risk metrics, helping inform decision-making and maintain regulatory compliance.
Workflow Automation: Seek third-party risk management software that offers workflow automation to streamline routine tasks such as distributing comprehensive risk assessments and surveys. Automation should also facilitate formal processes for approvals, escalations, and action management, reducing human error and improving efficiency.
Vendor Risk Scoring: Choose a platform that offers vendor risk scoring, providing scores based on industry benchmarks to give a clear view of potential risks and ensure high-quality vendor relationships.
Compliance Management: Ensure the vendor compliance management software you select includes robust compliance management features to verify that third-party vendors adhere to relevant regulations and standards, minimizing legal and regulatory risks.
Incident Management: Look for vendor risk management providers with incident management capabilities to track, manage, and resolve incidents involving third parties in a timely and documented manner.
Supplier Audits: Opt for vendor risk management tools that support comprehensive supplier audits, allowing for easy comparisons between vendors and the risks they pose – ensuring SLAs are on track.
Business Continuity Capabilities: Select vendor risk management companies with platforms that offer business continuity features to help you assess and manage third-party risks that could impact your organization’s continuity and resilience.
Vendor or supplier risk management differs from traditional risk management by specifically focusing on the risks arising from third-party vendors and suppliers. It involves evaluating, monitoring, and mitigating risks associated with external partnerships through specialized software that automates key processes. This includes conducting vendor risk assessments, distributing questionnaires and surveys, analyzing vendor profiles and relevant news, tracking vendor performance against SLAs and KPIs, and formalizing the onboarding and offboarding of suppliers. This approach streamlines the different stages of the third-party lifecycle and ensures continuous oversight of vendor compliance, performance, and potential risks, making it particularly effective for managing complex third-party relationships.
In contrast, traditional integrated risk management has a broader focus, addressing a wide range of internal organizational risks such as operational, financial, strategic, cybersecurity, and regulatory risks. It requires maintaining an active risk register, conducting regular risk assessments, implementing controls, monitoring and testing those controls, and managing risk remediation efforts. While traditional risk management may include some assessment of third-party risks, it typically lacks the specialized tools and processes used in vendor risk management. As a result, traditional risk management approaches may be less efficient and comprehensive when it comes to handling the specific risks associated with vendors. Although these processes have varying differences they can both usually be managed in the same GRC platform.
Vendor management involves managing various risks related to the third-parties your organisation works with – including cybersecurity, compliance, financial stability, operational performance, and reputational damage. Cybersecurity risks like data breaches, supply chain attacks, and vendor vulnerabilities can compromise an organization’s security. Non-compliance with regulations, vendor insolvency, and poor-quality products or services can lead to legal, financial, and operational issues. Reputational risks also arise if vendors engage in unethical practices or fail to meet expectations, which can damage a company’s brand. Geopolitical instability, natural disasters, and communication barriers further complicate vendor relationships.
To mitigate these risks, organizations should conduct thorough due diligence, establish clear contracts, and implement ongoing monitoring of vendor performance, compliance, and risk exposure. This includes automating risk assessments, tracking vendor performance against SLAs and KPIs, and integrating external risk intelligence sources for real-time insights. Having a structured vendor risk management process helps identify potential threats early, ensures compliance, and protects the organization from disruptions, legal issues, and financial losses.
Get started and request a demo
Fill out our simple form to see the Camms vendor risk management software in action.
